Today@Dal
» Go to news mainBecome Scam Smart: Learn how to spot some of the current phishing scams making the rounds right now

The spring 2024 email phishing season is in full swing, and we have been made aware of some of current scams circulating in the community. Have you received any seemingly suspicious messages in your inbox? It's essential you remain vigilant in protecting yourself, your data, and your community.
Follow along to learn about some of the current phishing emails in circulation: Virtual Assistant, Employee Gift Card and Document Signing.
Virtual Assistant
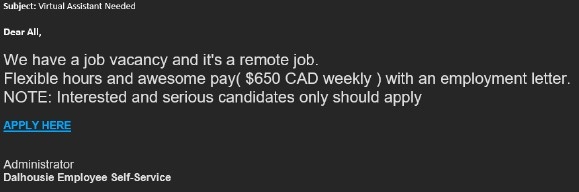
Characteristics:
- An unsolicited job opportunity with a “professor/recruiter” approaches someone at Dal over email.
- The email comes from a personal account, such as Gmail, or is sent from a Dal email but then redirected to a Google form or some other non-Dal service (SMS, Skype, iChat, etc.) to “apply” for the opportunity.
- They accept your resume and offer a position without any interview.
- Often, the work will involve “administrative tasks,” such as finding the price of items in a store and purchasing gift cards. The sums of money offered range from $300 to $800 for a few hours of work.
- They ask you to purchase items and gift cards with your own money.
Employee Gift Card
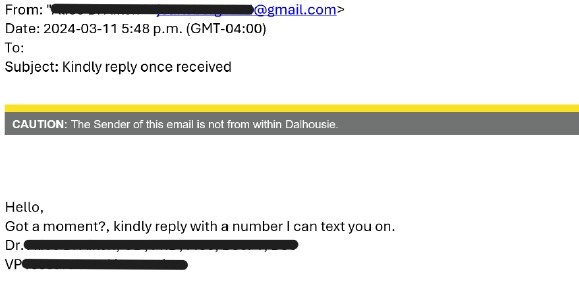
Characteristics:
- A supervisor, manager, or department head reaches out to an employee via email or text, but not from their normal email or phone number.
- They claim to be in a meeting and need you to take care of something urgently before they get out of it - so they can’t talk to you directly.
- They ask you to purchase gift cards or online vouchers with your own money and claim they will reimburse you.
Document signing
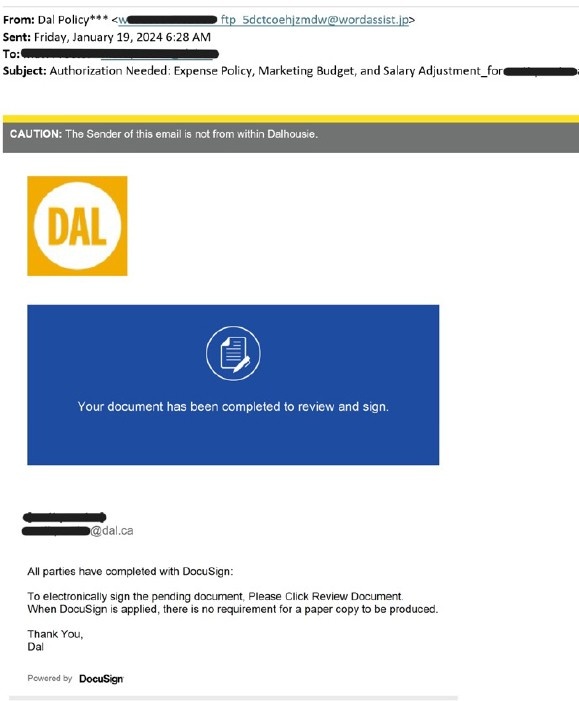
Characteristics:
- A document attachment or link that you weren’t expecting shows up in email.
- It claims to be an approval for something financially important.
- The sender is unclear, or from outside of the organization.
These examples, and similar messages, are phishing scams being widely distributed across higher-ed environments in North America. Universities are once again seeing a spike in fake messages offering jobs, asking for urgent action, or threatening consequences if you don’t act now.
General phishing scam patterns to watch for
- An urgent call to action or threats – Be suspicious of messages that claim you must click, call, or open an attachment immediately. Often, they'll claim you have to act now to claim a reward or avoid a penalty.
- First time or infrequent senders– It's not unusual to receive a message from someone for the first time, especially if they are outside your network, but this can be a sign of phishing. Always be cautious with first time or infrequent contacts.
- Mismatched email domains– If a message claims to be from a reputable company, like Microsoft or your bank, but the email is being sent from another email domain like Gmail.com, or microsoftsupport.ru it's probably a scam. Also be watchful for very subtle misspellings of the legitimate domain name, like micros0ft.com where the second letter "o" has been replaced by a zero. These are common tricks of scammers called “typosquatting”.
- Suspicious links or unexpected attachments – Always be careful if you receive an attachment you weren’t expecting – even from someone you know. If you suspect that an email message is a scam, don't open any links or attachments that you see. Sometimes the scam can be revealed by hovering your mouse pointer over any links to see if they lead to a suspicious web location.
What happens if I respond to it?
Phishing messages often try to get you to log in to a malicious website, so that they can steal your password. Once they have your password, they will try to trick you into approving an MFA (multi-factor authentication) request on your phone or security device, so that the malicious actor can access your account.
Other times they will try to get you to open a file which will load malicious software on your device. They may deliver this file after they have started a conversation with you (where you are “hooked” and interacting with them). The file may be given to you as an “update on your account” or a “copy of your transcript/invoice/receipt,” but it instead installs malicious software on your device that can watch what you do, or even control your device remotely.
The most likely outcomes from continued interaction with a phishing scammer will be:
- They will hijack your account and use it to phish others
- They will use your information to pretend to be you (identity theft) for other financial criminal activities
- They will try to defraud you by:
- Gaining access to your bank account by claiming to need the information in order to pay you or reimburse you for some activity
- Get you to send them money directly, either for fake job equipment or as a reimbursement for a large deposit they faked making into your bank account
- Convince you to commit crimes on their behalf – such as cashing phony checks at business locations
What should I do if I receive a phishing email?
- The best thing to do if you are concerned about a potential phish is to throw the message away if it has suspicious indicators.
- If you’ve accidently opened a potential malicious attachment, or entered your password on a potentially malicious site, you have a second chance! Be especially watchful for any new MFA prompts on your account that aren’t for a login on a device that you recognize, and change the password on your account immediately. Then reach out to your IT support for additional guidance.
Guidance to help members of our community with online scams:
- Report any obvious scam emails at Dal via the Outlook web client available on https://my.dal.ca. You can open the web application of your Outlook from the App menu on myDal (which looks like a Rubik’s cube in the upper left corner). From Outlook on the web, right-click on the scam email, and select “Report/Report Phishing” from the menu that pops up. That will help train our email system to get better at detecting scams as they change methods and senders.
- Be especially cautious with any messages arriving in your Dal inbox that contain a banner at the top of an email which states “CAUTION: The Sender of this email is not from within Dalhousie.” That is an indicator that the person sending you a note may not be who they claim. This is especially important when the person supposedly sending the message works for the institution.
- Double check the email address of a sender to see if it comes from an inappropriate account for that person (such as a Gmail account rather than a Dal account), especially if they are asking you to take an action regarding:
- Access to systems or resources
- Financial transactions
- Requests for personal information or sensitive institutional information
- When you have a request from someone asking you to take action in the areas above (financial/personal info/access), verify with that person via a different communications method - which you know they should control - to make sure you are talking to them. As examples:
- Call their office or cell phone after finding their contact method through a Dal department or a trusted individual (don’t use the contact given in the initial email)
- Chat with them on Teams at Dal, or start up a video call with them
- Stop by their office to verify that they sent you the message
- For departments and people involved in regular financial or sensitive data work, consider establishing a “code word” or approval phrase that should be stated when confirming that person’s identity.
- This is a new recommendation coming from Public Safety Canada’s latest advice on financial fraud against institutions, through the Canadian Center for Cyber Security. As we get into more uses of AI for remote deception online, it will become harder and harder to establish identity using someone’s voice or appearance online. Families and organizations are encouraged to start establishing “code phrases” or “family safe-words” to establish identities for people you know… even if someone looks/sounds just like the person you know in an online medium.
- This is a bit of an “old school” tactic to confirm safety before taking action – similar to the way some families have a “family word” that must be shared with a child before any relative/friend/acquaintance is allowed to pick them up or do something with them without prior arrangements.
- Stay up-to-date on phishing alerts. Check the Cyber Security Alerts section of myDal periodically to see if there is a persistent phishing campaign targeting the Dal community.
If you have questions on identifying a potential phish, please reach out to Dal’s IT Support groups for more information and assistance.